We use cookies to make your experience better. To comply with the new e-Privacy directive, we need to ask for your consent to set the cookies. Learn more.
Most modern microcontrollers include security features for locking or encrypting the debug interface, protecting read out, and more. Each silicon vendor has its own method of configuring and activating these features. The Device Provisioner for J-Link, J-Trace and Flasher takes care of unifying access to these options.
The Device Provisioner is a command line tool for the J-Link debug probes, J-Trace streaming probes and Flasher in-circuit programmers for setting up and configuring devices to ensure they are ready for use. The provisioning process involves tasks such as initializing hardware, installing necessary software, configuring settings, and sometimes associating the device with a specific user or network. The Device Provisioner is created as a command line tool to seamlessly integrate into automation environments.
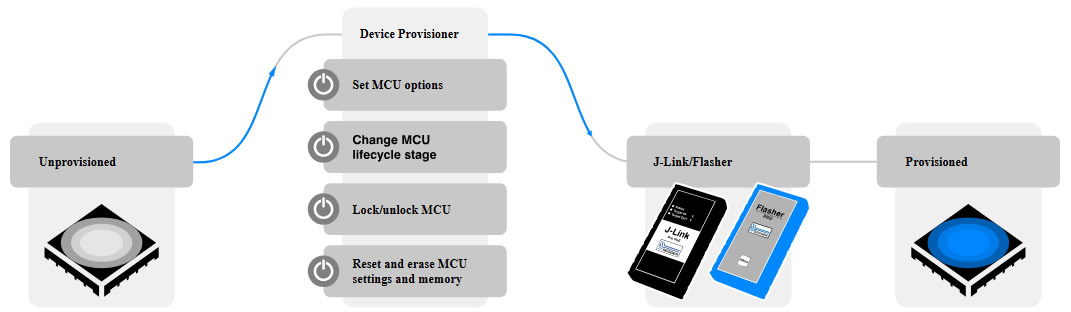
Use cases
Device provisioning for secure debugging
Secure microcontrollers offer options to debug over secured interfaces. To set up the interface properly, the Device Provisioner is used to set up the target device with secure IDs and to set the state to accept secure debug connection. This includes enabling the interfaces, activating security features for the interfaces (securing) or locking them down, once the product lifecycle reaches this state.
Device provisioning for secure programming
Secure programming usually requires preparation of the device by adding secure IDs and enabling the device to lock itself down after transmission of the firmware. The Device Provisioner provides commands to change the states of the microcontroller that enable or disable debugging or secure programming. In addition, the device provisioner can download keys or certificates (provisioning), if required for the secure processes.
Configuring TrustZone® partitions
TrustZone® is Arm’s tool for code isolation on a device. To prepare a target device, the trusted areas have to be configured. After adding code to the trusted partition, the zone can be locked such that no further read or write access is possible in the zone.
Example project
Secure product lifecycle management for the STM32H5 series
Device provisioning plays a foundational role in establishing and maintaining the security of devices throughout their lifecycle, from initial deployment to decommissioning. It ensures that devices are configured securely, managed effectively, and integrated seamlessly into the overall security infrastructure. SEGGER has already developed security product lifecycle features for the STM32H5 series from STMicroelectronics. It includes all necessary commands ranging from checking the product state to performing a full regression.
Discovery
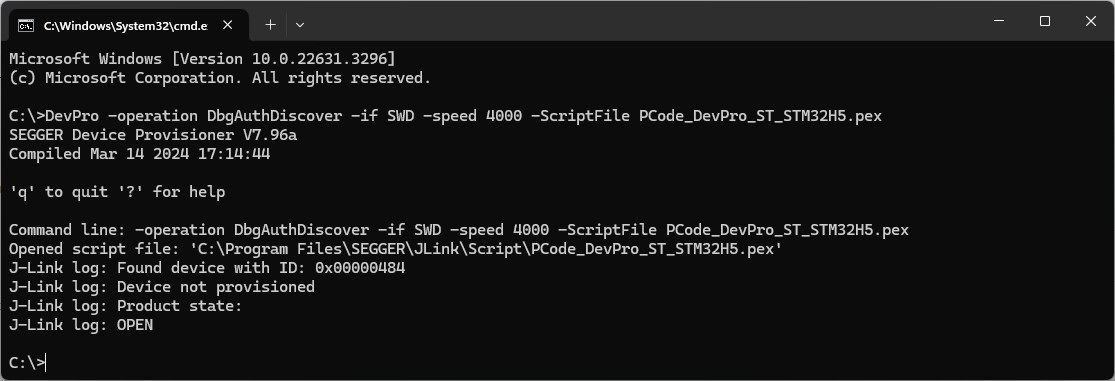
Product state change
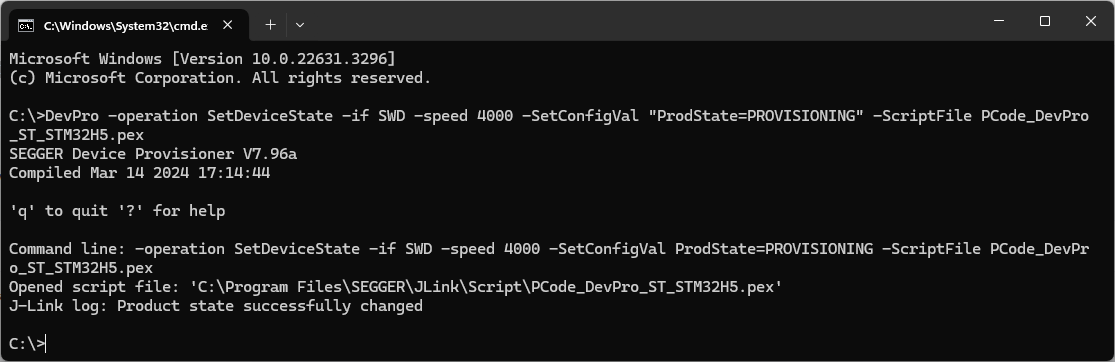
Provisioning
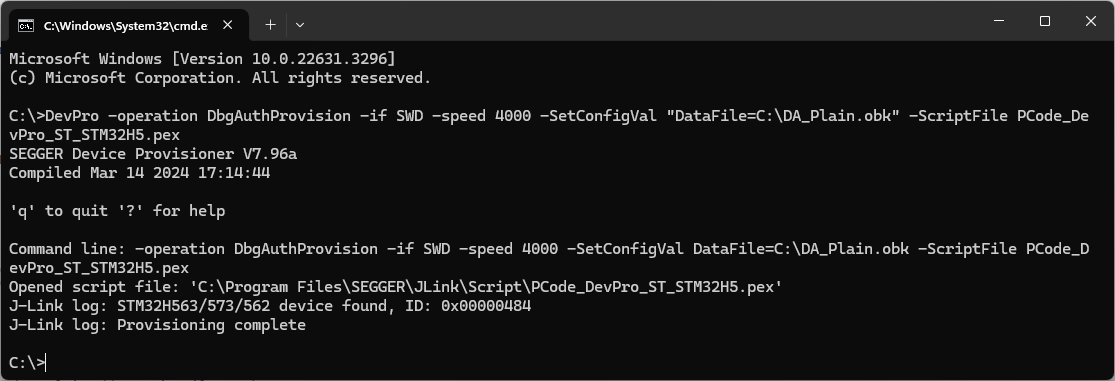
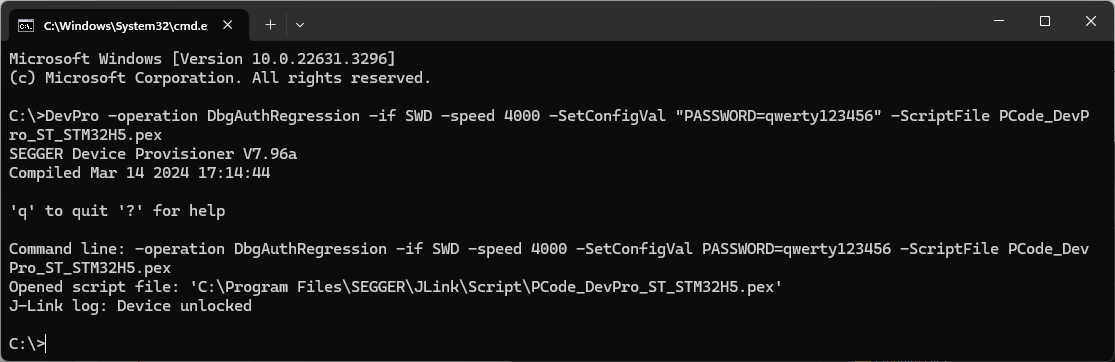
Unlocking
Script customization & flexibility
Customization requires a script. The Device Provisioner utility offers the utmost in flexibility by enabling users to customize their own device provisioning process by writing their own script.
SEGGER can also, upon request, help with the script or the script may come from the Silicon Vendor. The script required for popular MCUs is available from SEGGER and more will be added over time.
Interface access
The Device Provisioner has full access to interfaces of the J-Link debug probes, J-Trace streaming probes and Flasher in-circuit programmers interface, including but not limited to protocols such as JTAG, SWD, SPD, I2C, SPI, and UART.
Licensing
The Device Provisioner is included in both the J-Link Software and Documentation Package and the Flasher Software and Documentation Package. The software package is free for any J-Link, J-Trace or Flasher device and can be downloaded here.
- Ability to set up security features of MCUs
- Ability to set up debug and programming interfaces
- Ability to enable automation
- Ability to customize scripts
System requirements
| Supported OS | |
|---|---|
| Windows | Microsoft Windows (x86/x64) |
| macOS | macOS (x86/Apple Silicon) |
| Linux | Linux (x86/x64/Arm) |
Non esitare a metterti in contatto con i nostri esperti.
Basta chiedere qui