We use cookies to make your experience better. To comply with the new e-Privacy directive, we need to ask for your consent to set the cookies. Learn more.
emCrypt for Secure Applications
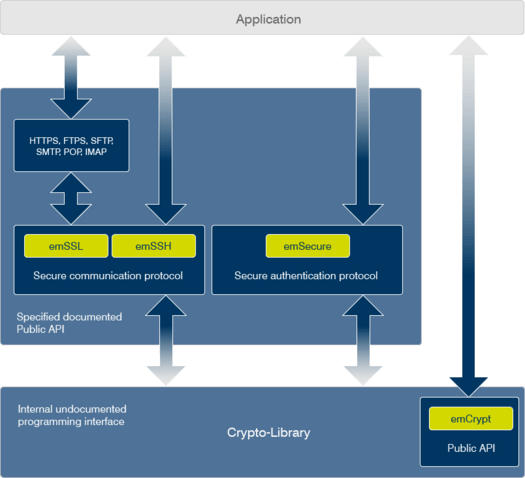
The Crypto-Library emCrypt provides the building blocks for today's secure protocols. Security has never been so important with the explosion of embedded devices that are now connected to the Internet. emCrypt has proven itself within SEGGER and is the foundation that emSSL, emSSH and emSecure-RSA, emSecure-ECDSA are built upon.
- emCrypt offers a wide range of cryptographic capabilities that are the basis of many security protocols.
- emCrypt can be configured for minimal memory footprint of constrained devices but can also scale to faster performance on systems that have more resources.
- emCrypt is a high-quality product, designed to be used easily but without limitations.
- emCrypt is not covered by an open-source or required-attribution license and can be integrated in any free, commercial, or proprietary product without the obligation to disclose the combined source.
- emCrypt is provided as source code and offers transparency for all included modules, allowing inspection by auditors.
- emCrypt is portable. The complete software is written in ANSI C and is compiler as well as target independent. It can be implemented in PC applications and in embedded designs.
- emCrypt is configurable. It is created for high performance and a low memory footprint. The library can be configured for size or speed. Unused features can be excluded, additional features can easily be added.
- emCrypt supports pluggable cryptographic algorithms and hardware acceleration. Hardware acceleration for popular microcontrollers is available as an option.
emCrypt is a complete package and comes with everything needed to secure communication for your embedded system.
It includes all modules which implement the required functionality to use SSH. They are provided in source code, to allow complete control of the code that is used in the product and create transparency to avoid worries about possible back doors or weakness in code, which cannot be checked in precompiled libraries.
emCrypt comes with a simple, yet powerful API to make using emCrypt in your product as simple as possible. It also includes sample applications in source form which demonstrate how to use the emCrypt API.
emCrypt-BASE Package Content
- AES-128, AES-192, AES-256
- DES
- TripleDES (also known as 3DES or TDES) with all keying options
- MD5
- RIPEMD-160
- SHA-1
- SHA-224, SHA-256. SHA-384, SHA-512, SHA-512/224, SHA-512/256
emCrypt-PRO Package Content
- All ciphers (AES, XTS-AES, DES, TripleDES, ARIA, SEED, Camellia, Blowfish, Twofish, IDEA)
- All hash algorithms (MD5, RIPEMD-160, SHA-1, SHA-2 family, SHA-3 family, SM3)
- All MAC algorithms (HMAC, CMAC, GMAC, KMAC, Michael)
- All key derivation algorithms (KDF1, KDF2, HKDF, PBKDF2, X9.63 KDF)
- All key agreement protocols (DH, ECDH, X25519, X448)
- All digital signature protocols (RSASSA-PSS, RSASSA-PKCS1, DSA, ECDSA, Ed25519, Ed448)
- All key generation algorithms, probabilistic and proven primes, for RSA and DSA
- All random bit generators (Fortuna, Hash_DRBG, HMAC_DRBG, CTR_DRBG)
- All extendable output functions (SHAKE128, SHAKE256, cSHAKE128, cSHAKE256)
- All key encapsulation functions (RSAES-OAEP, AESKW, Camellia-KW, ARIA-KW, SEED-KW, Twofish-KW)
- All NIST prime curves (P-192, P-224, P-256, P-384, P-521)
- All Brainpool curves and twisted curves (brainpoolP160r1 through brainpoolP512r1)
- All self-test
- Supports modern cryptography standards
- NIST-validated implementations of many algorithms
- Secure, fast, and cleanly-written code
- Extensive 2,000 page manual covering all API features and functions
- Decoupled implementation links only what you need
- Public key cryptography (RSA, DSA, ECDSA, EdDSA)
- Fast, tunable ciphers, hash algorithms, and message authentication codes (MACs)
- Key derivation, key wrapping, key encapsulation
- Random bit generation, cryptographically secure pseudo-random numbers
Tecnologix offers support which is directly handled by development team. Do not hesitate to get in touch with our experts.
Just ask here